contemporary security studies
Contemporary Security Studies
The definitive introduction to security studies, focusing on key theoretical approaches and the critical issues shaping today''s global security landscape. Contemporary Security Studies offers a uniquely engaging introduction to Security Studies, addressing key theories and contemporary issues in the field. A team of expert scholars strikes a careful balance between depth and clarity, making it an essential companion for students exploring the modern security agenda.Key features:· Offers broad, easy-to-digest coverage of the key theories and concepts in Security Studies · Brings together carefully edited contributions from international experts in the field, giving students insights from a range of leading scholars · ''Think point'' boxes challenge students to question their own assumptions, and help to develop critical thinking skills · Case study boxes encourage students to connect theory and practice by demonstrating the real-world manifestations of political issues · Includes coverage of critical Security Studies perspectives, including poststructuralism, postcolonialism, and post-human.· Considers a broad range of traditional and non-traditional security issues, from inter-state armed conflict and nuclear weapons to security issues centring on the environment, crime and cyber-attacks· Also available as an e-book with functionality, navigation features, and links that offer extra learning supportNew to this edition:· Chapter 3 provides a ... Unknown localization key: "more"
Objev podobné jako Contemporary Security Studies
Security Studies: Critical Perspectives - Kyle Grayson, Xavier Guillaume
The only introduction to critical security studies to take a question-centred approach, with a unique emphasis on equipping students with the knowledge and skills to think, analyse, and debate using critical perspectives. Security Studies: Critical Perspectives introduces the analysis of security from critical and interdisciplinary perspectives. Taking a student-centred approach to understanding contemporary security themes and cases, it provides an accessible set of analytic steps so that students develop the critical thinking skills and confidence to ask important questions about security and our worlds in contemporary politics. Common-sense security assumptions that reproduce forms of oppression and domination are revealed and their justifications decentred while perspectives inclusive of class, gender and sexualities, ethnicity and race, religion, disability, culture and ideology, political belonging, and the global south are introduced. In doing so, the authors combine critical analysis with concrete empirical issues that connect students to the social and political worlds around them. Five foundation chapters introducing students to key concepts and methodologies Fifteen thematic chapters, written by leading security analysts exploring key themes in security Detailed illustrative cases for each thematic chapter Accessible short introductions, in the online resources, to some of the major theoretical approaches in critical security studies Online resources ... Unknown localization key: "more"
Objev podobné jako Security Studies: Critical Perspectives - Kyle Grayson, Xavier Guillaume
Security Studies
Security Studies: An Applied Introduction offers a transformative tool to understand, analyse, and engage with the complexities of security in the modern world. This groundbreaking new text redefines the landscape of security studies with the following features: Policy-Relevant: each chapter provides analysis of policy responses to empirical security issues. This practical approach offers a toolkit to assess and contribute to real-world policy discussions. Empirical Application: vividly demonstrating the real-world relevance of Security Studies with online videos from leading security practitioners to show how theory informs practice. Pedagogically Rich: comprehensive online resources and chapters features such as ′security beyond the real′ and hands-on exercises that critically assess real-world security responses and their policy implications that offer ways to apply theoretical concepts in a highly innovative way. Innovative Structure: seamlessly integrating theoretical perspectives with empirical security concerns, this textbook offers a non-compartmentalised approach to theory and practice. Hot Topics: placing contemporary, creative, emerging, and underexplored approaches and empirical topics at the forefront including cyber security, racism, and space security. This is the perfect introduction for undergraduate and postgraduate students studying Security Studies and International or Global Security. Malte Riemann is Assistant Professor in Contemporary Armed Conflict, Leiden University, the Netherlands  Norma ... Unknown localization key: "more"
Objev podobné jako Security Studies
Podívejte se také
židle Duo Studio Stone pro studenty
nehtové studio pro děti
Crazy Chic Cool nehtové studio
hravé nehtové studio pro holky
nehtové studio s rychlosušičkou
čerpadlo pro studnu a zahradu
dubové nástěnné hodiny Studio
exkluzivní hodiny od Studia Stefanutti
čerpadlo pro zavlažování ze studny
velké tetovací studio pro děti
čerpání vody ze studny do 8 metrů
židle Duo Studio Carrara 68x46 cm
koš POKER SET pro studia
žárovka GX9.5 230V pro studiové světlo
DJ Studio Pro pro začátečníky i profesionály
Thin Lizzy 1977 studiové album
Contemporary Terrorism Studies
- When do individuals radicalise? - Can terrorism be rational? - How can we define terrorism? - What is the role of women in terrorism? - Can states be terrorist? World leading experts answer these questions in Contemporary Terrorism Studies, the first textbook to provide a multi-disciplinary, methodologically plural, and richly diverse introduction to terrorism studies. Contemporary Terrorism Studies covers the main approaches in terrorism studies, and is structured into three comprehensive sections. The first on ''The State of Terrorism Studies'' maps the development and historical context of the discipline, and looks to the future of terrorism studies. Part two on ''Issues and Debates in Terrorism Studies'' examines key contentious questions and debates such as the role of women, technology, and the media in terrorism. The final part, part three on ''Countering Terrorism'' focuses specifically on counterterrorism: it''s instruments, foreign policy, legal frameworks, and organisations. Overall, text will engage students, and establish a confident understanding of the subject. The textbook has been developed with pedagogical features to help enhance student learning. Each chapter contains case studies to highlight real world examples of political violence, questions for reflection to encourage critical thinking, and suggestions for further reading which provide useful sources ... Unknown localization key: "more"
Objev podobné jako Contemporary Terrorism Studies
Contemporary British Studio Pottery - Ashley Thorpe
Pots have existed across the world and in different cultures for thousands of years. This volume explores how contemporary makers use the ancient language of the pot to convey contemporary ideas, from the sculptural and painterly to the ecological and satirical. This beautifully produced book is a visually rich and critically in-depth focus on the work of twenty-four potters. A companion volume to Contemporary British Ceramics: Beneath the Surface, it reveals how pots can be extraordinarily powerful forms of expression.
Objev podobné jako Contemporary British Studio Pottery - Ashley Thorpe
Security in 21st Century Europe - Andrew Cottey
Russia’s 2022 invasion of Ukraine, the rise of populism and uncertainties about the future direction of US politics and foreign policy have created a troubling new international environment for Europe. Against this background, Security in 21st Century Europe explores the evolution of European security since the end of the Cold War and the security challenges facing European states in the 2020s and beyond. It argues that security in Europe has been transformed by the development of liberal regional order underpinned by a security community – a zone of peace where war is inconceivable – and NATO and the EU. But today the European security community, NATO and the EU face a growing array of external challenges and even questions about their continued existence. This third edition analyses:- The relationship between the European security community/NATO/EU and the wider Europe, including: Russia; the Balkans; the former Soviet space; the Mediterranean and North Africa- European engagement with core thematic security issues, including: military intervention; nuclear weapons; terrorism; and non-military security- 3 new chapters on migration, climate change and cybersecurity- All recent major developments that impact on European security, including: the Syrian civil war and resulting regional destabilization; the Russia-Ukraine war; China’s accelerating rise; ... Unknown localization key: "more"
Objev podobné jako Security in 21st Century Europe - Andrew Cottey
Avast Premium Security pro 1 počítač na 12 měsíců (elektronická licence) (prw.1.12m)
Avast Premium Security je elektronická licence poskytující komplexní antivirovou ochranu pro jeden počítač s operačním systémem Windows po dobu 12 měsíců. Produkt nabízí ochranu před širokým spektrem internetových hrozeb včetně ransomware a falešných webů. Licence je dodávána elektronicky a aktivuje se přes uživatelský účet.
- Kompletní online ochrana pro 1 zařízení na 12 měsíců
- Největší síť pro detekci hrozeb na světě s cloudovou AI
- Blokuje viry a ransomware v reálném čase
- Automatické aktualizace a behaviorální analýza
Objev podobné jako Avast Premium Security pro 1 počítač na 12 měsíců (elektronická licence) (prw.1.12m)
Exam Ref SC-200 Microsoft Security Operations Analyst - Sarah Young, Yuri Diogenes, Jake Mowrer
Tato příručka připravuje kandidáty na Microsoft certifikační zkoušku SC-200 Security Operations Analyst. Pokrývá klíčové oblasti jako mitigaci hrozeb pomocí Microsoft 365 Defender, Microsoft Defender for Cloud a Microsoft Sentinel. Předpokládá předchozí zkušenosti se správou, monitorováním a reakcí na hrozby v prostředích Microsoft 365.
- Komplexní příprava na oficiální Microsoft certifikaci SC-200
- Zaměření na praktické dovednosti pro bezpečnostní operace
- Strukturováno podle oficiálních zkušebních cílů
- Zahrnuje strategické scénáře pro rozvoj kritického myšlení
Objev podobné jako Exam Ref SC-200 Microsoft Security Operations Analyst - Sarah Young, Yuri Diogenes, Jake Mowrer
Stabilization and Human Security in UN Peace Operations - Alexander Gilder
UN peace operations are increasingly asked to pursue stabilization mandates with lofty expectations of being able to stabilize conflict zones, achieve national reconciliation, and rebuild state legitimacy. This book investigates the relationship between UN stabilization mandates and the concept of ‘human security’.The book is divided into three parts. Part I outlines the emergence of stabilization and other trends in peacekeeping practice and outlines an analytical framework of human security. Part II applies the analytical framework to case studies of MINUSMA, MINUSCA, and UNMISS examining issues, such as human rights, empowerment, protection, and vulnerability. In Part III the book draws out several concerns that arise from stabilization mandates, including the militarisation of UN peace operations and the consequences under international humanitarian law, the risks of close cooperation with the host state and engagement in counter-terror activities, and the potential clash between peacebuilding activities and militarisation.The book will be a valuable resource for academics, policymakers and practitioners working on UN peacekeeping generally, and those specifically looking at stabilization, from the perspective of international relations, international law, peace and conflict studies, security studies and human rights.
Objev podobné jako Stabilization and Human Security in UN Peace Operations - Alexander Gilder
Gibson Les Paul Studio Heritage Cherry Sunburst
Gibson Les Paul Studio Heritage Cherry Sunburst je elektrická kytara kombinující esenciální design Les Paul s prvky pro aktivní hráče. Disponuje odlehčeným tělem, push/pull humbuckery a kombinací mahagonového těla s javorovým topem. Je určena především pro pódium a studiové nahrávání.
- Odlehčené tělo pro pohodlné hraní
- Push/pull humbuckery pro univerzální zvuk
- Kombinace mahagonového těla a javorového topu
- Cenově dostupnější než vyšší modely Les Paul
Objev podobné jako Gibson Les Paul Studio Heritage Cherry Sunburst
Mac Studio M1 MAX (Z14J0003Q)
Počítač Apple Mac Studio M1 MAX je výkonná stolní pracovní stanice s čipem Apple Silicon. Disponuje 32 GB operační paměti, 512 GB SSD disku a 32jádrovou grafickou kartou. Nabízí rozsáhlé konektivity včetně HDMI, USB-C a Thunderbolt portů.
- Extrémně výkonný čip Apple M1 MAX s 32jádrovou GPU
- Velká operační paměť 32 GB pro náročné úlohy
- Rychlý SSD disk 512 GB s bezkonkurenční rychlostí
- Bohatá konektivita: HDMI, USB-C, Thunderbolt, 2× USB 3.2
Objev podobné jako Mac Studio M1 MAX (Z14J0003Q)
Spin Master Cool Maker náhradní balení pro vlasové studio růžové
Toto náhradní balení je doplňkovou sadou pro vlasové studio Cool Maker od Spin Master. Obsahuje copánkovou čelenku, postranní vlasový příčesek nebo 2 drdoly a 1 culík. Je určeno pro děti od 8 let a slouží k tvorbě a zdobení vlasů.
- Růžová barva atraktivní pro děti
- Obsahuje více typů příčesků (čelenka, drdoly, culík)
- Snadné použití s vlasovým studiem Cool Maker
- Vhodné pro kreativní hru od 8 let
Objev podobné jako Spin Master Cool Maker náhradní balení pro vlasové studio růžové
HM Studio Dětský kostým pro princezny, 130-140 cm
Dětský karnevalový kostým princezna od HM Studio obsahuje šaty a spodničku. Kostým je vyroben z 100% polyesteru a je vhodný pro děti ve věku 8-10 let s výškou 130-140 cm. Balení má rozměry 4 x 24 x 31 cm.
- Kompletní kostým včetně šatů a spodničky
- Vhodné pro věk 8-10 let (velikost 130-140 cm)
- Kvalitní materiál 100% polyester
- Ideální pro karnevaly a tematické akce
Objev podobné jako HM Studio Dětský kostým pro princezny, 130-140 cm
Spin Master Cool Maker náhradní balení pro vlasové studio fialové
Toto náhradní balení je doplňkovou sadou pro vlasové studio Cool Maker od Spin Master. Obsahuje copánkovou čelenku, postranní vlasový příčesek nebo 2 drdoly a 1 culík. Je určeno pro holčičky od 8 let k tvorbě a zdobení účesů.
- Kompatibilní s vlasovým studiem Cool Maker
- Obsahuje více typů příčesků (čelenka, drdoly, culík)
- Vhodné pro kreativní hru dětí od 8 let
- Atraktivní fialová barva
Objev podobné jako Spin Master Cool Maker náhradní balení pro vlasové studio fialové
Clementoni Crazy Chic Nehtové studio
Clementoni Crazy Chic Nehtové studio je kreativní sada určená pro holčičky od 6 let. Obsahuje kompletní příslušenství pro péči a zdobení nehtů včetně třpytkového stroje, laků, třpytek a samolepek. Sada funguje na 2 AA baterie, které nejsou součástí balení.
- Kompletní kreativní sada pro péči a zdobení nehtů
- Obsahuje třpytkový stroj, laky, třpytky a samolepky
- Vhodné pro děti již od 6 let věku
- Podporuje rozvoj jemné motoriky a kreativity
Objev podobné jako Clementoni Crazy Chic Nehtové studio
Alltoys Nehtové studio jednorožec
Nehtové studio s motivem jednorožce je sada pro holčičky od 6 let, která obsahuje 12 nalepovacích nehtů, lak na nehty a ozdobné kamínky. Umožňuje dětem vytvářet originální nehtové designy. Balení má rozměry 18 x 15 x 2 cm.
- Kompletní sada pro dětskou manikúru s motivem jednorožce
- Obsahuje 12 nalepovacích nehtů, lak a ozdobné kamínky
- Bezpečné a vhodné pro děti již od 6 let
- Podporuje kreativitu a hravé učení péče o sebe
Objev podobné jako Alltoys Nehtové studio jednorožec
Židle Duo Studio Stone 68 x 46 x 90,5 cm
Kancelářská židle Duo Studio Stone o rozměrech 68 × 46 × 90,5 cm nabízí ergonomický design a praktické funkce pro pracovní a studijní prostředí. Disponuje výškově nastavitelným sedákem, pěti kolečky a odolnou plastovou skořepinou. Díky kompaktním rozměrům a decentnímu vzhledu je vhodná i do menších prostor.
- Výškově nastavitelný sedák pro individuální přizpůsobení
- Ergonomicky tvarovaná opěrka zad pro pohodlné sezení
- Pětiramenný kříž s kolečky zajišťující mobilitu a stabilitu
- Snadno čistitelný plastový povrch pro jednoduchou údržbu
Objev podobné jako Židle Duo Studio Stone 68 x 46 x 90,5 cm
Židle Duo Studio Carrara 68 x 46 x 90,5 cm
Kancelářská židle Duo Studio Carrara o rozměrech 68 × 46 × 90,5 cm nabízí ergonomický design a praktické funkce pro pracovní i studijní prostředí. Disponuje výškově nastavitelným sedákem, pětikolovou základnou a snadno čistitelným plastovým povrchem. Je vhodná pro domácí kanceláře, studentské pokoje i menší prostory.
- Výškově nastavitelný sedák pro individuální přizpůsobení
- Ergonomicky tvarovaná opěrka zad pro pohodlí při dlouhém sezení
- Pětikolová základna zajišťující stabilitu a snadný pohyb
- Snadná údržba díky odolnému plastovému povrchu
Objev podobné jako Židle Duo Studio Carrara 68 x 46 x 90,5 cm
Rosefield The Studio Edition 01 SBGSG-O66
Hodinky Rosefield The Studio Edition 01 SBGSG-O66 představují limitovanou edici s automatickým strojkem. Model disponuje modrým ciferníkem a koženým řemínkem. Výrobek splňuje standardy voděodolnosti do 5 ATM.
- Limitovaná edice s exkluzivním designem
- Automatický švýcarský strojek s vysokou přesností
- Kožený řemínek prémiové kvality
- Voděodolnost do 5 ATM pro každodenní nošení
Objev podobné jako Rosefield The Studio Edition 01 SBGSG-O66
MAC Cosmetics Studio Radiance Serum-Powered Foundation hydratační make-up odstín NC11 30 ml
MAC Studio Radiance Serum-Powered Foundation je středně krycí hydratační make-up s obsahem 10% kyseliny hyaluronové. Produkt poskytuje až 12hodinový zářivý efekt, neucpává póry a je odolný vůči vodě a potu. Je vhodný pro všechny typy pleti a dermatologicky testovaný.
- Hloubkově hydratuje pleť až 24 hodin díky 10% kyselině hyaluronové
- Poskytuje až 12hodinový zářivý efekt bez maskovacího vzhledu
- Neucpává póry, je otěruvzdorný a odolný vůči vodě a potu
- Obsahuje 33 pečujících složek včetně vitaminu E a jojobového oleje
Objev podobné jako MAC Cosmetics Studio Radiance Serum-Powered Foundation hydratační make-up odstín NC11 30 ml
MAC Cosmetics Studio Fix Conceal And Correct Palette korekční paletka odstín Deep 6 g
Korekční paletka MAC Studio Fix Conceal And Correct Palette poskytuje střední až plné krytí pro korekci tónu pleti. Produkt spolehlivě kryje tmavé kruhy, akné, znaménka i tetování a je vhodný pro všechny typy pleti. Textura je jemná, snadno se nanáší a je dermatologicky i oftalmologicky testována.
- Střední až plné krytí vydrží až 24 hodin
- Nezvýrazňuje vrásky a jemné linky
- Vhodná pro všechny typy pleti, nezpůsobuje akné
- Obsahuje vitaminy E a C jako antioxidanty
Objev podobné jako MAC Cosmetics Studio Fix Conceal And Correct Palette korekční paletka odstín Deep 6 g
Walachia Zvonice a studna
Stavebnice Walachia Zvonice se studnou obsahuje 68 dřevěných a papírových dílků pro slepení modelu historické lidové architektury. Součástí balení je schematický montážní plán a informace z historie stavebnictví. Model po sestavení má rozměry 9 x 9 x 17 cm a je vhodný pro děti od 8 let.
- Rozvíjí zručnost a logické uvažování
- Příjemný dřevěný materiál
- Dobře opracované dílky – minimální potřeba broušení
- Obsahuje historický popis lidové architektury
Objev podobné jako Walachia Zvonice a studna
HM Studio Dětský kostým netopýr 130-140 cm
Dětský karnevalový kostým netopýr od HM Studio je určen pro děti ve věku 8-10 let s velikostí postavy 130-140 cm. Kostým se skládá z pláště s límcem a kapucí, overalu s gumou v pase a pásku na suchý zip s vycpanými svaly. Materiál je 100% polyester, délka overalu je 114 cm a šířka v pase 40 cm.
- Kompletní kostým s pláštěm, kapucí a overalem
- Pohodlný střih s gumou v pase
- Snadné nasazení díky suchému zipu
- Vycpané svaly pro autentický vzhled
Objev podobné jako HM Studio Dětský kostým netopýr 130-140 cm
Clementoni Crazy Chic nehtové studio sprej, pero
Kreativní sada Clementoni Crazy Chic nehtové studio obsahuje pistoli na třpytky a pomůcky pro zdobení nehtů. Je určena pro dívky od 6 let a umožňuje vytvářet originální nehtové designy. Sada funguje na 2 AA baterie, které nejsou součástí balení.
- Kompletní kreativní sada s pistolí na třpytky
- Návod pro snadné nanášení laků a třpytek
- Vhodné pro děti již od 6 let
- Možnost vytváření originálních nehtových designů
Objev podobné jako Clementoni Crazy Chic nehtové studio sprej, pero
HM Studio Šachy společenská hra
Klasická společenská hra šachy od HM Studio je určena pro dva hráče a vhodná pro děti od 6 let. Sada obsahuje hrací desku a 32 figurek. Hra podporuje rozvoj logického a strategického myšlení.
- Rozvíjí soustředění a strategické uvažování
- Vhodné pro děti od 6 let
- Obsahuje kompletní sadu 32 figurek a hrací desku
- Klasická společenská hra pro dva hráče
Objev podobné jako HM Studio Šachy společenská hra
Alltoys Nehtové studio s Pop It kabelkou
Nehtové studio s Pop It kabelkou je hrací sada pro holčičky od 6 let, která obsahuje 12 nalepovacích nehtů, 24 nálepek, lak na nehty a ozdobné kamínky. Sada umožňuje vytvářet originální nehtové designy a rozvíjí kreativitu. Balení má rozměry 18 x 15 x 2 cm.
- Kompletní sada pro kreativní manikúru včetně 12 nalepovacích nehtů a 24 nálepek
- Pop It kabelka pro stylové uložení a přenášení všech doplňků
- Obsahuje lak na nehty a ozdobné kamínky pro originální designy
- Vhodné pro děti od 6 let, podporuje jemnou motoriku a kreativitu
Objev podobné jako Alltoys Nehtové studio s Pop It kabelkou
L.O.L. Surprise! OMG Nehtové studio s panenkou - Pinky Pops Fruit Shop
L.O.L. Surprise! OMG Nehtové studio s panenkou Pinky Pops Fruit Shop je hračka obsahující kompletní sadu pro manikúru. Součástí jsou nalepovací nehty, laky, třpytky, samolepky a módní doplňky pro panenku. Hračka je vhodná pro děti od 4 let a panenka měří přibližně 25 cm.
- Kompletní nehtové studio s více než 15 překvapeními včetně laků, pilníku a samolepek
- Obsahuje módní doplňky pro panenku - náušnice, boty a 3 doplňky
- Vhodné pro kreativní hru a rozvoj jemné motoriky u dětí od 4 let
Objev podobné jako L.O.L. Surprise! OMG Nehtové studio s panenkou - Pinky Pops Fruit Shop
Alltoys Nehtové studio s náramkem
Sada Alltoys Nehtové studio obsahuje 12 nalepovacích nehtů, pilníček, prstýnek a náramek pro kreativní hru. Je vhodná pro děti od 6 let a rozvíjí jejich jemnou motoriku. Rozměry balení jsou 21 x 14 x 2 cm.
- Kompletní kreativní sada pro péči o nehty
- Obsahuje 12 nalepovacích nehtů a doplňky
- Bezpečné pro děti od 6 let
- Rozvíjí jemnou motoriku a kreativitu
Objev podobné jako Alltoys Nehtové studio s náramkem
Focusrite Scarlett Solo Studio 4th Gen
Focusrite Scarlett Solo Studio 4th Gen je kompletní záznamový balíček pro sólové hudebníky obsahující USB zvukovou kartu, kondenzátorový mikrofon a sluchátka. Čtvrtá generace přináší vylepšený zvuk a optimalizované ovladače pro nahrávání bez latence. Balíček je ideální pro domácí nahrávací studio zpěváků a hudebníků.
- Kompletní balíček obsahující zvukovou kartu, mikrofon a sluchátka
- Vylepšený zvuk 4. generace s křišťálově čistým záznamem
- Nulová latence při nahrávání díky optimalizovaným ovladačům
- Kvalitní kardioidní kondenzátorový mikrofon vhodný pro zpěv a nástroje
Objev podobné jako Focusrite Scarlett Solo Studio 4th Gen
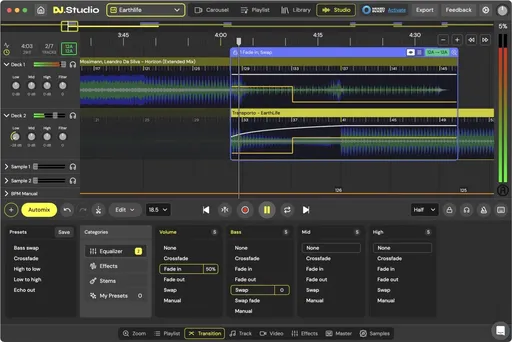
DJ.Studio Pro
DJ Studio Pro je sofistikovaný software pro DJing určený začátečníkům i pokročilým uživatelům. Umožňuje přípravu živých setů, rozhlasových pořadů a videomixů přímo z notebooku. Software využívá přes 200 tisíc DJů od amatérů po profesionály.
- Intuitivní uživatelské rozhraní vhodné pro všechny úrovně
- Funkce Automix pro automatickou úpravu playlistů podle tempa a harmonie
- Editor přechodů na časové ose pro precizní mixování
- Všestranné využití pro živé sety, rozhlasové pořady i videomixy
Objev podobné jako DJ.Studio Pro
MAC Cosmetics Studio Waterweight SPF 30 Foundation lehký hydratační make-up SPF 30 odstín NW 13 30 ml
MAC Studio Waterweight SPF 30 Foundation je lehký hydratační make-up s ochranou proti slunci. Nabízí lehké až střední krytí s dlouhou výdrží a gelovou texturou, která neslévá do vrásek. Produkt je dermatologicky a oftalmologicky testován.
- Velmi lehká gelová textura bez efektu masky
- SPF 30 chrání pleť před UV zářením po celý den
- Hydratační komplex pro přirozeně vlhkou a svěží pleť
- Snadná aplikace pipetou a rozetření do ztracena
Objev podobné jako MAC Cosmetics Studio Waterweight SPF 30 Foundation lehký hydratační make-up SPF 30 odstín NW 13 30 ml
HM Studio Cestovní Námořní bitva
HM Studio Cestovní Námořní bitva je strategická hra pro dva hráče, kde cílem je sestřelit všechny lodě soupeře pomocí souřadnic. Hra je vyrobena z plastu a je vhodná pro děti od 4 let. Balení obsahuje dvě hrací pole, lodě, červené a bílé kolíčky a smolepky.
- Cestovní verze s praktickým obalem, který slouží jako hrací pole.
- Vhodné pro děti již od 4 let, podporuje strategické myšlení.
- Kompletní vybavení včetně lodí, kolíčků a smolepek pro snadné hraní.
- Rychlá hra s dobou hraní 15-30 minut, ideální na cesty.
Objev podobné jako HM Studio Cestovní Námořní bitva
CCEA GCSE Business Studies, Third Edition - Hope Kerr
Exam Board: CCEALevel: GCSESubject: BusinessFirst Teaching: September 2017First Exam: June 2019This title has been endorsed for use with the CCEA GCSE Business Studies specificationInspire student success with Hope Kerr''s market-leading Student Book; fully revised for the 2017 specification, it supports and engages learners through up-to-date content coverage and case studies relevant to local, national and global contexts.- Helps students learn and apply key business concepts and theories by providing clear explanations, accompanied by diagrams and photos that aid understanding- Enables students to consolidate their knowledge as they work through a range of activities for each topic- Increases interest and engagement by including contemporary case studies with a particular focus on Northern Ireland businesses and contexts- Prepares students for the new examinations with practice questions, guidance on how to answer different question types and an overview of the assessment objectives and command words- Allows students to track their progress and target their revision using the end-of-chapter checklists
Objev podobné jako CCEA GCSE Business Studies, Third Edition - Hope Kerr
HM Studio Dětský kostým Pavouk 92-104 cm
Dětský kostým Pavouk od HM Studio je karnevalový oblek pro chlapce od 4 let, inspirovaný podobou pavoučího hrdiny. Kostým je vyroben z 100% polyesteru a je dostupný ve velikosti 92-104 cm. Boty nejsou součástí balení.
- Autentický design inspirovaný pavoučím hrdinou
- Vyrobeno z pohodlného a snadno udržovatelného materiálu
- Ideální pro karnevaly, narozeninové oslavy a hraní
Objev podobné jako HM Studio Dětský kostým Pavouk 92-104 cm
Glitterific glitter studio
Glitterific glitter studio je kreativní sada pro vytváření třpytivých tetování na různé předměty jako školní batohy nebo čepice. Sada obsahuje pero s funkcí nanášení a odsávání třpytek, samolepicí archy s předlohami a třpytky ve dvou barvách. Produkt je určen pro děti od 6 let a není vhodný pro aplikaci na kůži.
- Pero s dvojím režimem pro nanášení i odsávání přebytečných třpytek
- Kompletní sada s více barvami třpytek a předlohami tetování
- Bezpečné pro děti od 6 let, vhodné na školní potřeby a textil
- Jednoduchá aplikace pomocí samolepicích archů
Objev podobné jako Glitterific glitter studio
Style4Ever Kreativní studio 3 v 1
Kreativní sada 3 v 1 umožňuje dětem od 6 let zdobit deníky pomocí nálepek, vyřezávat reliéfy na papír a kreslit tvary pomocí šablon. Balení obsahuje všechny potřebné materiály pro tyto tři techniky. Rozměry balení jsou 34 x 31 cm.
- Víceúčelová sada 3 kreativních technik v jednom balení
- Rozvíjí jemnou motoriku a fantazii dětí od 6 let
- Všechny potřebné materiály včetně šablon a nálepek
- Ideální pro zdobení deníků a zápisníků
Objev podobné jako Style4Ever Kreativní studio 3 v 1
Alltoys Výroba náramků Art Studio 6 ks
Kreativní sada Art Studio obsahuje 26 doplňků včetně ozdob, přívěsků, kamínků a provázků pro výrobu náramků a náhrdelníků. Sada je určena pro děti od 6 let a pomáhá rozvíjet představivost a zručnost. Materiály zahrnují plast a karton.
- Rozvíjí představivost a kreativitu
- Trénuje trpělivost a jemnou motoriku
- Obsahuje vše potřebné pro výrobu šperků
- Vhodné pro děti od 6 let
Objev podobné jako Alltoys Výroba náramků Art Studio 6 ks
HM Studio Kreslící tabulka rybka 2 v 1
Kreslící tabulka ve tvaru ryby nabízí dětem plochu pro kreslení nebo razítkování. Po smazání obrázku pomocí mazací lišty mohou děti opětovně tvořit. Výrobek je vhodný pro děti od 3 let a je vyroben z plastu.
- Rozvíjí kreativitu a vizuální vnímání dětí
- Praktická mazací lišta pro snadné opakované použití
- Atraktivní design ve tvaru ryby pro děti
- Vhodné pro děti již od 3 let věku
Objev podobné jako HM Studio Kreslící tabulka rybka 2 v 1
Alltoys Tetovací studio s copánky
Tetovací sada Alltoys je kreativní hračka pro holky od 6 let, která umožňuje vytvářet dočasná tetování a ozdoby do vlasů. Obsahuje šablony, barevná pera, kamínky a ozdoby pro všestrannou zábavu. Balení má rozměry 29 x 4 x 25 cm.
- Kompletní sada pro kreativní hru s tetováním a ozdobami do vlasů
- Vhodné pro děti od 6 let, podporuje jemnou motoriku a fantazii
- Obsahuje šablony, barevná pera a kamínky pro různé vzory
- Bezpečné a snadno omyvatelné dočasné tetování
Objev podobné jako Alltoys Tetovací studio s copánky
Alltoys Tetovací studio s šablonami
Tetovací studio Alltoys je kreativní sada pro dívky od 6 let, obsahující tetovací pera, kamínky, šablony a kosmetickou taštičku. Umožňuje vytvářet barevné vzory na těle a vlasech, které jsou snadno omyvatelné. Balení má rozměry 25 x 3 x 21 cm.
- Kompletní sada s tetovacími pery, kamínky a šablonami
- Vhodné pro kreativní hru od 6 let, podporuje jemnou motoriku
- Praktická kosmetická taštička pro snadné uskladnění
- Bezpečné a snadno omyvatelné ozdoby na tělo a vlasy
Objev podobné jako Alltoys Tetovací studio s šablonami
Epee Airbrush studio jednorožec
Kreativní sada umožňující dětem od 6 let dekorovat plyšové zvířátko pomocí airbrush techniky. Součástí balení je plyšák, sprejovací nástroj, tři barevné náplně, 120 plastových šablon a ochranné rukavice. Plyšové zvířátko je pratelné ve studené vodě a po zaschnutí připraveno k dalšímu tvoření.
- Rozvíjí kreativitu a jemnou motoriku dětí
- Plyšáka lze po zaschnutí opakovaně přestříkávat
- Kompletní sada obsahuje vše potřebné včetně ochranných pomůcek
- Snadné použití s připraveným airbrush nástrojem a šablonami
Objev podobné jako Epee Airbrush studio jednorožec
Alltoys Tetovací studio set
Tetovací studio set je kreativní sada pro holky od 6 let, která obsahuje třpytivá tetování, kamínky, šablony a barevná tetovací pera. Umožňuje ozdobit vlasy i tělo barevnými vzory. Balení má rozměry 25 x 3 x 21 cm.
- Vhodné pro děti od 6 let, bezpečné a zábavné
- Obsahuje třpytivá tetování, kamínky, šablony a barevná pera
- Podporuje kreativitu a hru s kamarády
- Snadné použití pro ozdobu vlasů a těla
Objev podobné jako Alltoys Tetovací studio set
Melissa & Doug make up studio
Melissa & Doug Make Up Studio je kreativní sada pro děti od 3 let obsahující 16 realistických maket kosmetických doplňků. Děti si mohou vyzkoušet práci vizážistky bez použití skutečných líčidel. Sada podporuje rozvoj fantazie, jemné motoriky a tvořivosti.
- Realisticky zpracované makety kosmetiky (16 kusů)
- Bezpečná hračka pro děti již od 3 let
- Rozvíjí fantazii, jemnou motoriku a tvořivost
- Nápaditá sada s mnoha herními možnostmi
Objev podobné jako Melissa & Doug make up studio
Studies in Ethnomethodology - Harold Garfinkel
This is the first appearance in paper back of one of the major classics of contemporary Sociology. Studies in Ethnomethodology has inspired a wide range of important theoretical and empirical work in the social sciences and linguistics.
Objev podobné jako Studies in Ethnomethodology - Harold Garfinkel
Contemporary Conflict Resolution - Harmonie Toros, Tom Woodhouse, Oliver Ramsbotham, Hugh Miall
The indispensable guide to conflict resolution in a troubled world  At a time of mounting turmoil in world politics, conflict prevention and resolution, peacekeeping, and peacebuilding have never been more important as priorities on the global agenda. The wars in Ukraine and Gaza, and tensions between the major powers in what is now a multi-polar world, require new conflict resolution responses. The fifth edition of this hugely popular text offers a commanding overview of today’s changing conflict landscape and the latest developments and new ideas in the field. Fluently written in an easy-to-follow style, it guides readers carefully through the key concepts, issues and debates, evaluates successes and failures, and assesses the main challenges for conflict resolution today. To counter the prevailing patterns of transnational conflict, the book argues for a response based on cosmopolitan conflict resolution, grounded in the promotion of the cosmopolitan values on which the welfare and life hopes of future generations depend.  Comprehensively updated and illustrated with lively new case studies throughout, the fifth edition returns to its favoured twelve-chapter format. It remains the go-to text for students of peace and security studies, conflict management and international politics as well as policy-makers and those ... Unknown localization key: "more"
Objev podobné jako Contemporary Conflict Resolution - Harmonie Toros, Tom Woodhouse, Oliver Ramsbotham, Hugh Miall
iGET SECURITY M3P22 RFID klíč - používá se společně klávesnicí M3P13v2, pro alarm M3/M4
iGET SECURITY M3P22 - RFID klíčRFID klíč iGET SECURITY M3P22 je určen pro klávesnici iGET SECURITY M3P13v2. Tato klávesnice poté ovládá alarm iGET SECURITY M3 a M4. Stačí pouze přiložit tento klíč ke klávesnici iGET SECURITY M3P13v2 a zvolit zdali se má alarm iGET SECURITY M3 a M4 aktivovat nebo deaktivovat. Velmi snadné použití vhodné pro všechny členy vaší domácnosti. Díky malým rozměrům a úchytu je možné jej připevnit tam, kde je třeba. Hlavní parametryjednoduché rozšíření základního setu alarmu iGET SECURITY M3 a M4,navýšení stupně bezpečnosti při použití klávesnice iGET SECURITY M3P13v2 a RFID klíče iGET SECURITY M3P22 pro vzdálené ovládání, jelikož hlavní jednotka alarmu může být ukrytá,pomocí RFID klíče je možné alarm aktivovat a deaktivovat,RFID klíč nepotřebuje žádné napájení - není nutná výměna baterie,alarm iGET SECURITY M3 a M4 je tak možné ovládat pomocí klávesnice iGET SECURITY M3P13v2 společně s RFID klíčem iGET SECURITY M3P22, také pomocí klíčenky iGET SECURITY M3P5, a pomocí mobilní aplikace iGET SECURITY. Stav se vždy synchronizuje na všech zařízeníchSpecifikacePracovní frekvence: 125 kHzProvozní teplota: -30°C ~ +60°CProvozní vlhkost: 5% ~ 100%Rozměry a hmotnost: 28 x 28 mm, hmotnost 4,1 g
Objev podobné jako iGET SECURITY M3P22 RFID klíč - používá se společně klávesnicí M3P13v2, pro alarm M3/M4
The Security Culture Playbook - Kai Roer, Perry Carpenter
Mitigate human risk and bake security into your organization’s culture from top to bottom with insights from leading experts in security awareness, behavior, and culture. The topic of security culture is mysterious and confusing to most leaders. But it doesn’t have to be. In The Security Culture Playbook, Perry Carpenter and Kai Roer, two veteran cybersecurity strategists deliver experience-driven, actionable insights into how to transform your organization’s security culture and reduce human risk at every level. This book exposes the gaps between how organizations have traditionally approached human risk and it provides security and business executives with the necessary information and tools needed to understand, measure, and improve facets of security culture across the organization. The book offers: An expose of what security culture really is and how it can be measuredA careful exploration of the 7 dimensions that comprise security culturePractical tools for managing your security culture program, such as the Security Culture Framework and the Security Culture Maturity ModelInsights into building support within the executive team and Board of Directors for your culture management programAlso including several revealing interviews from security culture thought leaders in a variety of industries, The Security Culture Playbook is an essential resource for ... Unknown localization key: "more"
Objev podobné jako The Security Culture Playbook - Kai Roer, Perry Carpenter
Exam Ref AZ-500 Microsoft Azure Security Technologies, 2/e - Orin Thomas, Yuri Diogenes
Prepare for Microsoft Exam AZ-500: Demonstrate your real-world knowledge of Microsoft Azure security, including tools and techniques for protecting identity, access, platforms, data, and applications, and for effectively managing security operations. Designed for professionals with Azure security experience, this Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified: Azure Security Engineer Associate level. Focus on the expertise measured by these objectives: Manage identity and access Implement platform protection Manage security operations Secure data and applications This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you have expertise implementing security controls and threat protection, managing identity and access, and protecting assets in cloud and hybrid environments About the Exam Exam AZ-500 focuses on the knowledge needed to manage Azure Active Directory identities; configure secure access with Azure AD; manage application access and access control; implement advanced network security; configure advanced security for compute; monitor security with Azure Monitor, Azure Firewall manager, Azure Security Center, Azure Defender, and Azure Sentinel; configure security policies; configure security for storage and databases; and configure and manage Key Vault. About Microsoft Certification Passing this exam fulfills your requirements for ... Unknown localization key: "more"
Objev podobné jako Exam Ref AZ-500 Microsoft Azure Security Technologies, 2/e - Orin Thomas, Yuri Diogenes
Cyber Security Management and Strategic Intelligence - Peter Trim, Yang-Im Lee
Within the organization, the cyber security manager fulfils an important and policy-oriented role. Working alongside the risk manager, the Information Technology (IT) manager, the security manager and others, the cyber security managerÂ’s role is to ensure that intelligence and security manifest in a robust cyber security awareness programme and set of security initiatives that when implemented help strengthen the organizationÂ’s defences and those also of its supply chain partners.Cyber Security Management and Strategic Intelligence emphasizes the ways in which intelligence work can be enhanced and utilized, guiding the reader on how to deal with a range of cyber threats and strategic issues. Throughout the book, the role of the cyber security manager is central, and the work undertaken is placed in context with that undertaken by other important staff, all of whom deal with aspects of risk and need to coordinate the organizationÂ’s defences thus ensuring that a collectivist approach to cyber security management materializes. Real-world examples and cases highlight the nature and form that cyber-attacks may take, and reference to the growing complexity of the situation is made clear. In addition, various initiatives are outlined that can be developed further to make the organization less vulnerable to attack. Drawing ... Unknown localization key: "more"
Objev podobné jako Cyber Security Management and Strategic Intelligence - Peter Trim, Yang-Im Lee
Tribe of Hackers Security Leaders - Jennifer Jin, Marcus J. Carey
Tribal Knowledge from the Best in Cybersecurity Leadership The Tribe of Hackers series continues, sharing what CISSPs, CISOs, and other security leaders need to know to build solid cybersecurity teams and keep organizations secure. Dozens of experts and influential security specialists reveal their best strategies for building, leading, and managing information security within organizations. Tribe of Hackers Security Leaders follows the same bestselling format as the original Tribe of Hackers, but with a detailed focus on how information security leaders impact organizational security. Information security is becoming more important and more valuable all the time. Security breaches can be costly, even shutting businessesand governments down, so security leadership is a high-stakes game. Leading teams of hackers is not always easy, but the future of your organization may depend on it. In this book, the world’s top security experts answer the questions that Chief Information Security Officers and other security leaders are asking, including: What’s the most important decision you’ve made or action you’ve taken to enable a business risk?How do you lead your team to execute and get results?Do you have a workforce philosophy or unique approach to talent acquisition?Have you created a cohesive strategy for your information security program ... Unknown localization key: "more"
Objev podobné jako Tribe of Hackers Security Leaders - Jennifer Jin, Marcus J. Carey